


According to the Ministry of Internal Affairs of Georgia (MIA), on 1 September 2020, a cyberattack was carried out on the Ministry of Health, Labor and Social Affairs of Georgia from a foreign country. The primary goal of the cyberattack was the illegal seizure and use of the documents of the central apparatus of the Ministry and its structural units, including the National Center for Disease Control and Public Health and the Richard Lugar Research Center, as well as the important information on the management of pandemic. As MIA reports, a part of the authentic documents, obtained as a result of the cyberattack, is uploaded on one of the foreign websites and is available for the public use. Additionally, the purposefully falsified documents, that are aimed at intimidating the society and fostering confusion and distrust, are uploaded on the same website.
Although MIA does not specify the country from which the cyberattack was carried out, the processes and disinformation campaign that preceded the accident indicate the Russian trace with high probability. More specifically, it is notable that the Russian government and propaganda channels have been promoting the disinformation campaign against the Lugar Laboratory for years. The disinformation campaign became even more active during the Coronavirus pandemic. Soon, the Russian officials also made the statements against the Lugar Laboratory. On 26 May 2020, the Ministry of Foreign Affairs of Russia declared that there were questions regarding the compatibility of the Lugar Laboratory with the Convention on Biological Weapons. Also, in May 2020, Russia addressed Georgia with the request to allow Russian experts’ access to the Lugar Laboratory and its documents without the presence of international or regional organizations. Therefore, it is highly logical to assume that the cyberattack on 1 September 2020 was carried out also by Russia.
Also, it is notable that in 2019, Russia carried out the cyberattack on Georgian servers. With regard to this cyberattack, it is said in the 2019 report of the State Security Service that “according to the information obtained through the investigation carried out by the Georgian side and its collaboration with international partners, the mentioned cyberattack was planned and carried out by the Administrative Unit of the Joint Staff of the Armed Forces of the Russian Federation. […] The cyberattack was aimed at violating the national security of Georgia, bringing harm to the citizens of Georgia and fostering tension in the society through interrupting the functioning of different organizations”. Therefore, the cyber operations carried out in Georgia as well as in other countries in recent years indicate the Russian trace in the cyberattack on the Georgian healthcare system.

The photo which appeared on Georgian websites during the Russian cyberattack
In recent years, the US and its partner countries – UK, Australia, New Zealand, Canada, Netherlands, Estonia, Lithuania, Macedonia, Germany, Bulgaria, Ukraine and Georgia ascribed the cyberattack to GRU. GRU - The Main Directorate of the General Staff of the Armed Forces is an intelligence unit of the Russian Federation, which produces recommendations for the Russian government to ensure the military security of the country. The consulting organization on information technologies, the largest contractor of the US intelligence, Booz Allen Hamilton published a report in March 2020, in which more than 200 cyberattacks carried out by the Russian hackers during the last 15 years (from 2004 until 202019) are studied. This report includes important and unique information about the functioning of the Russian hacking unit, the logic of the Russian cyber operations and how the Russian government uses them for fulfilling foreign policy objectives. Unlike the other similar researches that are focused on the specific cases of cyberattacks, this report creates a broader picture and analyzes the similar cases considering the political context.
As it is mentioned in the report of Booz Allen, GRU cyber operations have a specific logic which meets the principles defined in the Military Doctrine of the Russian Federation. This doctrine as well as the Foreign Policy concept is being regularly updated and republished by the Kremlin. The last Military Doctrine was published in 2014 and encompasses 23 threats and challenges, that require a response from the Russian army. These threats/challenges are as follows:
1. Expansion and strengthening of North Atlantic Treaty Organization (NATO)
2. Global or regional destabilization
3. Deployment of military forces adjacent to Russia or its allies
4. Undermining of Russian strategic deterrence capabilities
5. Violation of Russia’s or allies’ territorial integrity or sovereignty
6. Proliferation of weapons of mass destruction and missile technology
7. Failure to comply with international agreements and treaties
8. Armed conflict adjacent to Russia or its allies
9. Unauthorized use of foreign military force adjacent to Russia or its allies
10. Growth of transnational non-state threats like terrorism or organized crime
11. Growth of ethnic, religious, or cultural disagreements over territorial borders
12. Illicit use of cyber or information operations against Russia or its allies
13. Establishment of hostile states adjacent to Russia
14. State-sponsored subversive activities targeting Russia
15. Provocation of Russian political strife
16. Separatist and ethno-religious terrorism
17. Undermining of Russian historical, spiritual, and patriotic traditions
18. Provocation of Russian cultural strife
19. Sharp deterioration of interstate relations
20. Disruption of key Russian military capabilities or critical sectors
21. Support of armed insurrection in Russia or its allies
22. Use of military force during exercises adjacent to Russia or its allies
23. Heightened combat readiness
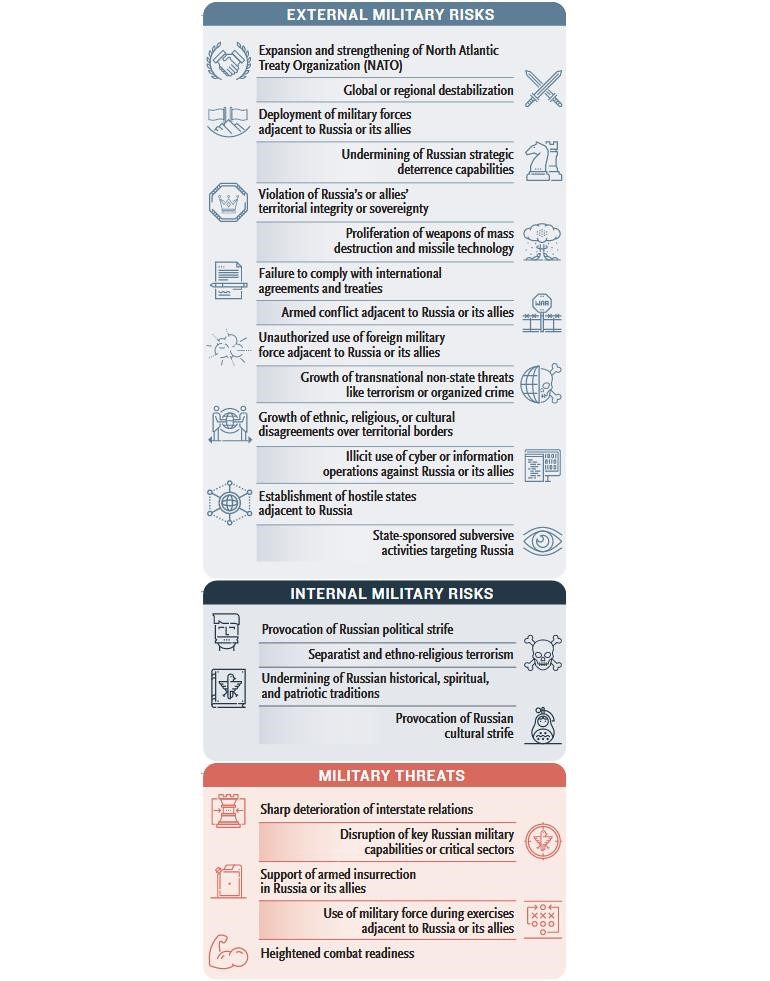
Source: Booz Allen Hamilton
In the 80-page report, the analysts of Booz Allen classified the cyberattacks carried out by Russia according to the above-mentioned 23 points, which shows that each cyberattack was linked with Russia’s security system, inferring the reaction to the ever-changing political environment around Russia.
Here we present some of the lesser-known cyberattacks carried out by Russia and analyzed by Booz Allen.
Syria
As it is mentioned in the report GRU supported Russian activities in Syria that were aimed at saving the Putin-friendly Assad regime. GRU’s operation is compatible with the 2nd point of the Kremlin Military Doctrine, encompassing the maintenance of steady political climate around Russia and the prevention of destabilization of Russia or its allies by foreign forces. From December 2014 until February 2015, GRU carried out the following operations:
- GRU’s operators attacked USA’s media outlets in order to create an impression that the Islamic State controlled a great number of cyber recourses.
- GRU’s operators published the personal data of the US military officers. Some of the data were obtained through hacking the US Military Central Command’s (CENTCOM) social media accounts.
- GRU hacked the Maryland television outlet’s text message alert system and sent threatening messages to subscribers
As a result of the above-mentioned operations, as it is mentioned in the report, the social support toward the US military activities in Syria decreased significantly and the US withdrew its forces from the region.
Montenegro
Russia interfered in Montenegro’s internal affairs when Montenegro expressed its willingness to join NATO. The cyber operations linked to this event are compatible with the 1st point of the Military Doctrine, focused on the expansion and strengthening of NATO.
GRU’s operations in Montenegro were aimed at supporting the pro-Russian political party in the elections and, in this way, interrupting the integration of the country in the NATO.
- Three days prior to the elections, GRU used so-called DDoS Attack – specific type of the cyberattack, through which the attacker attempts to make the internet recourse unavailable and interrupt user’s access to information. GRU attacked local media, NGOs, that were involved in the monitoring of the elections in Montenegro and state websites in order to cause chaos prior to the elections.
- Booz Allen mentions that GRU also used nongovernmental forces, which means the sponsoring of the pro-Russian political groups, clergy, NGOs and media.
- During the same period, GRU officers and agents, that were supposedly planning the attack on the Parliament, killing of the President and fostering the social arrest through the attacks on citizens, were arrested.
- After Montenegro joined NATO, GRU returned to hacking methods again.
Poland
GRU operations in Poland where Russia’s response to the allocation of NATO bases in the country. These operations are compatible with the 1st and 3rd points of the Military Doctrine – interference of NATO enlargement and deployment of foreign military bases near Russia. GRU carried out the following activities in Poland:
- Since spring 2014, GRU has been actively involved in monitoring of the Polish government and defense sector.
- GRU did this by using the so-called Watering Hole Attacks, meaning the identification of the websites that are being used by the target object/group/organization actively and attack them. Hackers linked to GRU used the automatized mechanism for attacking the Polish governmental and Defense websites, through which they gained access to the systems of all of the visitors of the websites.
- In 2018, when Russia suggested Belarus the deployment of Russian bases on its territories in response to the allocation of NATO bases in Poland and received a rejection from it, same hackers carried out so-called Spear-phishing operation against the Government of Belarus, meaning the targeted attack on individuals for gaining their personal data.
Romania
GRU’s hackers targeted Romania when the country increased in military expenses. Russian response to Romania’s decision is also compatible with the 3rd point od the Military Doctrine. In this case, the Black Sea region was a problem. For this, GRU used the following activities:
- when Romania initiated the creation of a united military unit with Moldova, GRU attacked the Embassy of Romania in Russia through Spear-phishing operations in order to receive detailed information about the upcoming activities.
- After Russia annexed Crimea in 2014, Romania started the modernization of the Black Sea Fleet. In a month, Russia still attacked a Romanian organization with Spear-phishing operation.
Denmark
GRU started the activities aimed against Denmark when the country declared that it joined the NATO Missile Defense System. This was the Russian response to the US steps, including the allocation of anti-missile systems near Russian borders and, therefore, undermining of Russian strategic deterrence capabilities (4th point of the Russian Military Doctrine).
- On 15 March, in one of his interviews, Russian Ambassador to Denmark said that Denmark’s joining to American anti-missile system would turn its ships into a target of Russian missiles.
- In ten days, GRU started a two-year operation, which included the hacking of the emails of the employees at the Ministry of Foreign Affairs and the Ministry of Defense of Denmark.
Ukraine
Since 2010, there have been talks in Ukraine about the schism between Russian and Ukrainian Orthodox Churches, which resulted in the announcement of autocephaly by the Ukrainian Church in 2018. The then-President of Ukraine, Petro Poroshenko called it the “main pillar of the independence of Ukraine”. Russia perceived this process as a threat as it violated the 17th point of the Military Doctrine - undermining of Russian historical, spiritual, and patriotic traditions. For this, GRU carried out the following operations:
- In 2012, an unidentified source published emails of a theologist of the Russian Orthodox Church who supported the independence of the Ukrainian Church. After this, he had to leave the church.
- Since 2015, GRU’s operators have been regularly attacking the emails of the clergy of the Eastern Orthodox Church, who was involved in schism, with Spear-phishing operations. The Chancellor of the American Orthodox Church (2015) and the assistants of the Archbishop of Constantinople (2018) were among the GRU’s targets.
International Sports Organizations
After the Russian sportsmen were banned from the Olympics and other sports events due to the doping scandal, GRU also targeted international sports organizations. As Booz Allen mentions, it was also perceived by Russia as a violation of the 17th point of the Military Doctrine. For this, GRU became involved and used the following means:
- In 2016, GRU hacked the World Anti-Doping Agency (Wada) and leaked foreign athletes’ therapeutic use exemptions.
- The operation likely sought to establish a false moral equivalency between the actions of Russian and foreign athletes. Russian media was also actively involved in spreading this narrative.
- GRU also attempted to carry out a cyberattack on the 2018 Winter Olympics, because the Russian athletes were still banned from it.
Conclusion
The above-listed cases of the cyberattacks are only a small part of the materials studied by Booz Allen. However, they create a background for understanding the system and logic of Russian cyber operations. Based on the conducted research, Booz Allen concludes that the Russian cyber operations are in direct correlation with the Russian Military Doctrine and international developments that violate ore or several points of this doctrine. Therefore, arguably, the cyber threats coming from Russia are predictable to some extent. Also, even though the MIA of Georgia does not specify the country from which the cyberattack on the Ministry of Health of Georgia was carried out, based on this report, it is possible to argue that it was in Russia’s interests. As the prior developments also indicated, Russia perceived the existence and successful functioning of the American laboratory next to its border as a threat, which violates the 14th point of Russia’s Military Doctrine.
The cyberattack on the Ministry of Health once again reveals that the consideration of the observations presented in Booz Allen’s report is essential for the Georgian reality. As the State Security Service of Georgia mentioned in its 2019 report, in parallel with the development of new technologies, the cyber capabilities of foreign countries increase, which is a challenge for the Georgian security and requires active collaboration with the strategic partners for improving cybersecurity and counterintelligence capabilities. It is important to note that the cyber risks from Russia increase amid the 2020 Parliamentary Elections. Therefore, it is essential to enhance the collaboration between decision-makers, civil sector and cybersecurity specialists in order to ensure the timely identification of such threats and implementation of the preventive measures.
___

This material has been financed by the Swedish International Development Cooperation Agency, Sida. Responsibility for the content rests entirely with the creator. Sida does not necessarily share the expressed views and interpretations.